Differences Between Penetration Testing and Vulnerability Scanning

Often, penetration testing (or pen testing) and vulnerability scanning are used interchangeably. In doing so, the importance of each method of testing gets lost in the confusion. Both of these are significant in protecting your data and infrastructure for different reasons.
In the age of digitally storing information and companies having an online network presence, it’s easy for hackers to find their way in. This is why both pen testing and vulnerability scanning are important.
Let’s take a look at each method and dissect them accordingly.
What Is Vulnerability Scanning?
Also known as vulnerability assessment, vulnerability scanning searches and assesses networks, systems, and computers for potential vulnerabilities. Typically, these scans are automated and focus on what vulnerabilities can be exploited. It is a comprehensive method to let you know about existing vulnerabilities and any changes since your last scan report.
A vulnerability assessment is recommended to be done quarterly or after infrastructure changes. The value of a vulnerability scanning is to detect how systems can be compromised.
Note that vulnerability scanning doesn’t go beyond reporting. Once these vulnerabilities are identified, it is up to the IT department to correct those weaknesses.
Vulnerability scans are beneficial, affordable, and quick to complete. As mentioned above, it can be automated, so it can be set up to run monthly or quarterly if desired.
It does come with some limitations, such as false positives. A false positive is when the scan indicates there is a vulnerability when there is not. However, there are ways to avoid this, such as having a reliable scanner that will rank risks by high, medium, or low.
What Is Penetration Testing?
Penetration testing is a controlled form of hacking, and is much more intense than vulnerability scanning. Unlike vulnerability scanning, it is not automated and requires a lot of tools and a human present. A pen test will simulate a hacker trying to get into your network, systems, and applications through the exploitation of vulnerabilities.
In other words, pen testing is known as “ethical hacking.” It is an authorized attack that is performed in order to evaluate the security of the system or application. It does more than just detecting equipment that has the potential to be compromised – it also shows potential business impact of those vulnerabilities if they were to be exploited by a cybercriminal.
Penetration testing covers the entire cycle shown below, whereas vulnerability scanning only covers the first three steps.
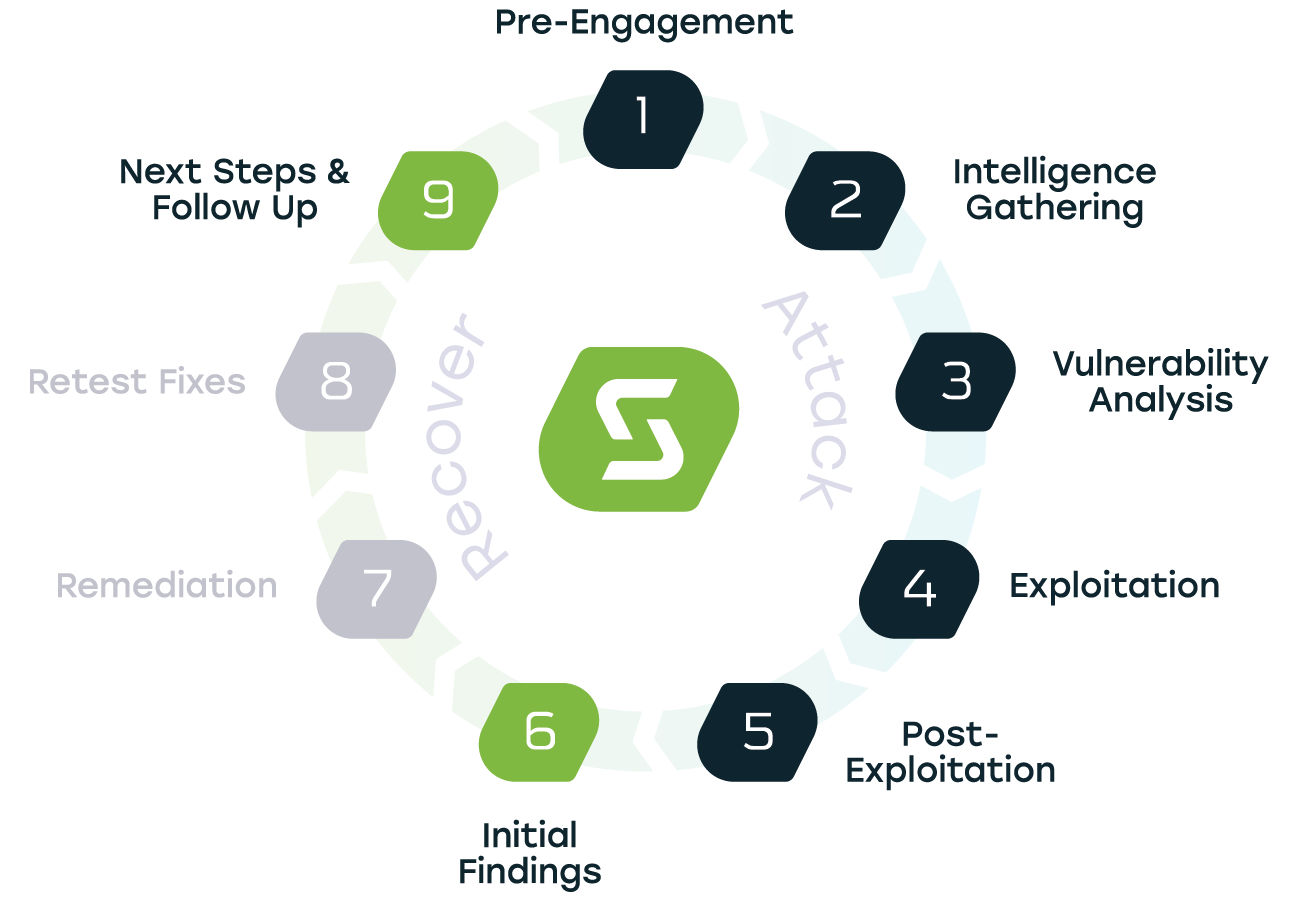
Look at a vulnerability scan and penetration testing as a person. The vulnerability scan peers through the windows of someone’s car, and checks to see if the door is open, but stops there. On the other hand, a penetration test goes further – it doesn’t just check to see if the door is open, but welcomes itself into the vehicle to size up what could be stolen and exactly how.
Pen testing shouldn’t be done too early on the network. During the deployment stage of a system, changes are happening, which makes pen testing ineffective since it won’t be able to catch all the holes in the security system. It’s best practice to conduct a pen test once the system is no longer constantly changing.
There are a few factors that play into the frequency of pen testing, such as company size, needs, budget, and regulations and compliance.
Which Method Is Preferred – Vulnerability Scan or Pen Test?
Both are crucial to an effective cybersecurity strategy. Performing monthly or quarterly vulnerability scans allows you to continuously identify and fix your more obvious vulnerabilities. A pen testing provides a thorough examination and can identify vulnerabilities that a scan cannot identify – these are typically done on an annual basis.
Penetration Testing and Vulnerability Scanning with Sedara
At Sedara, we can perform both penetration testing and vulnerability scanning tests for you. To find out the cost or to request a demo, contact us today.
Subscribe to Sedara Declassified to get timely updates on new and evolving threats–and what to do about them–just like our clients do.