A Guide to Cybersecurity Documentation

Introduction
The tip of the spear for every cybersecurity program should be a robust set of cybersecurity documentation that defines required activities and expected behavior. For most organizations, cybersecurity documentation includes policies, standards, and procedures, although other kinds, such as regulations and guidelines, may exist as well. The implementation of cybersecurity documentation is a governance control that can lessen risk and comply with legal and regulatory requirements. This article offers a guide on how organizations can create their own cybersecurity policies, standards, and procedures.
Why Create Documentation?
Many cybersecurity programs lack adequate documentation describing required activities and expected behavior. A lack of documentation exposes organizations to increased risk and reduces operational efficiency. For example, without documented policies organizations lack the ability to define program requirements and hold stakeholders accountable for adhering to requirements. And without documented procedures organizations lack the ability to communicate how to get things get done, exposing them to single points of failure if institutional knowledge holders ever leave the organization.
Cybersecurity documentation is so important that almost every cybersecurity framework includes documentation controls. For example, here’s only a few of the documentation controls included in popular cybersecurity frameworks:
- NIST CSF (GV.PO) – Organizational cybersecurity policy is established, communicated, and enforced
- NIST 800-53 (AC-1) – Develop, document, and disseminate…[an] access control policy…[and] procedures to facilitate the implementation of the access control policy
- CIS (15.2) – Establish and maintain a service provider management policy
- CISA CPG (2Q) – Implement an administrative policy or automated process that requires approval before new hardware, firmware, or software/software version is installed or deployed
Therefore, implementing cybersecurity documentation can help organizations reduce risk, improve outcomes, and comply with legal or regulatory requirements.
Policies, Standards, and Procedures
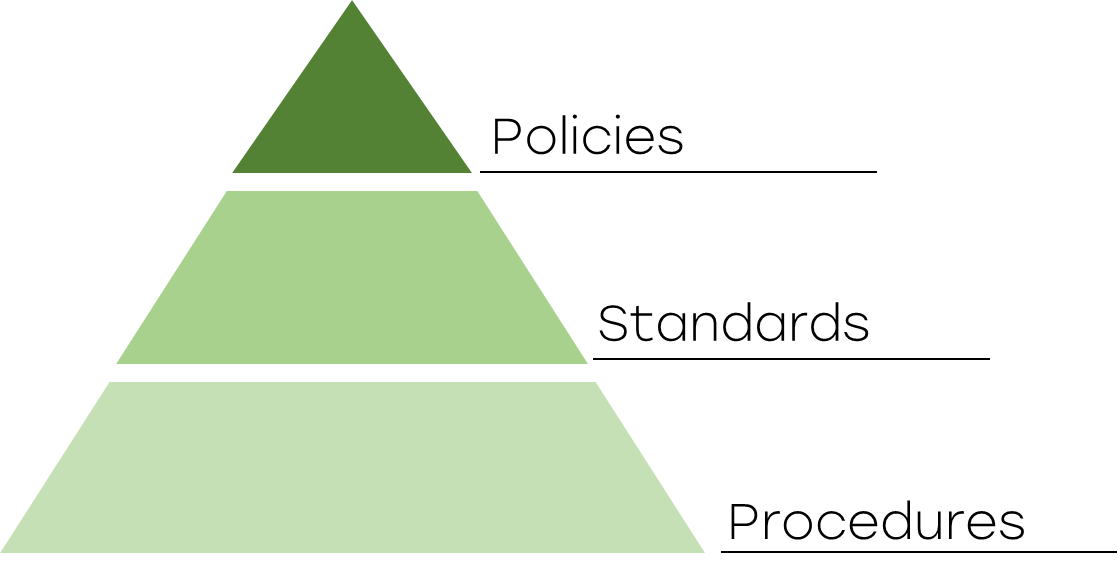
Cybersecurity documentation can be thought of as a hierarchy, with policies at the top, standards in the middle, and procedures at the bottom. Here’s a look at what each type of document is for, what role typically maintains it, and how often each document should be updated.
| Document Type | Purpose | Document Owner | Review Schedule |
| Policy | Describe what’s required (and why) | Executive Leadership, Board | Annually |
| Standard | Describe how to achieve the policy | IT Director, CTO, CIO | Quarterly or biannually |
| Procedure | Describe how to do the standard | Administrator, Engineer, Analyst | Ongoing |
In general, policies define high-level, non-negotiable programmatic requirements applicable to a broad stakeholder group. Standards define, at a lower, practical level, how to achieve the high-level policy requirement. Procedures define specific step-by-step instructions for achieving a standard. For example, an organization may document its vulnerability management program like this:
| Document Type | Vulnerability Scanning Documentation Example |
| Policy |
|
| Standard |
|
| Procedure |
|
This example shows how policies, standards, and procedures work together to define program requirements and operations. In this scenario we can imagine that executive leadership mandates vulnerability management through a policy, an IT director defines the specific requirements for the organization’s vulnerability management program through a standard, and IT technicians define how to perform specific vulnerability management operations through a procedure.
By documenting aspects of the cybersecurity program this way, organizations can ensure all stakeholders are involved in ensuring outcomes are clearly defined and achieved.
Other Considerations
When documenting all major components of a cybersecurity program across policies, standards, and procedures, organizations should also consider the following:
- Single or Plural – some organizations elect to have one overarching cybersecurity policy and procedure manual that encompass all aspects of the cybersecurity program (i.e., “one policy to rule them all”) while other organizations elect to have separate policies and procedures for each aspect of the cybersecurity program (i.e., “policy buffet”). Either approach is fine
- Write Clearly – policies, standards, and procedures should be written clearly so all stakeholders can easily understand them. However, keep in mind each document’s intended audience. Policies should be written in a way so all stakeholders understand them, including technical and non-technical readers. But it’s okay if procedures are written for a technical audience as they’re the only ones who might see them
- Review and Update – keep all policies, standards, and procedures up to date by following regular review cycles. No one wants to submit as part of an audit an outdated policy that does not reflect current organizational practices. Include a revision history section in each document to keep track of changes over time and the last review date
Conclusion
Overall, documentation is important part of every cybersecurity program. Documentation is type of governance control that reduces organizational risk, improves operational outcomes, and complies with legal and regulatory requirements. Documentation often manifests across policies, standards, and procedures, each of which are maintained by different stakeholder groups. Cybersecurity documentation can and should be implemented by all organizations, irrespective of their current maturity level. Technical controls are often erroneously associated with the most important type of cybersecurity control; organizations should not underestimate the importance of implementing robust cybersecurity documentation as part of their governance activities.
We Can Help
Sedara’s Cybersecurity Development Program (CDP) and its trained virtual Chief Information Security Officers (vCISOs) can help you build a successful cybersecurity program that reduces risk. Our vCISOs serve as your expert, trusted advisors on all things cyber and are skilled in all the major cybersecurity frameworks. We can help you develop your cybersecurity documentation based on our vast library of policy, standard, and procedure templates.
Additional resources:
Inside the Cloud: Attacks & Prevention – Administrative Account Compromise
NIST CSF 2.0 is Here. What Do You Need to Know?
How You Can Comply with NIST 800-171
Need more personalized security advice?