Malvertising: Phishing Edition

Malvertising: Phishing Edition
Online advertising is inevitable on countless websites and services across the Internet. Some attackers have learned to exploit online advertising services to deliver attacks, sometimes called “malvertising.”
There are sophisticated attacks in the wild that capture user credentials – even MFA – with a malicious sponsored link and exploit the resulting access.
How does it work?
In this type of malvertising, an attacker purchases an ad through a search engine like Google or Bing. They then use SEO (search engine optimization) techniques or ad customization to present their malicious ad in response to specified searched like “bank of usa login”.
Since sponsored results appear at the top of many search engine results, a distracted user can easily miss or ignore the “Sponsored” or “Ad” tag and click on the site. The site contains a phishing attack that appears like the legitimate site. The attacker’s goal is to collect credentials, credit card numbers, and other sensitive information.
A simulated example of this type of attack is shown here:
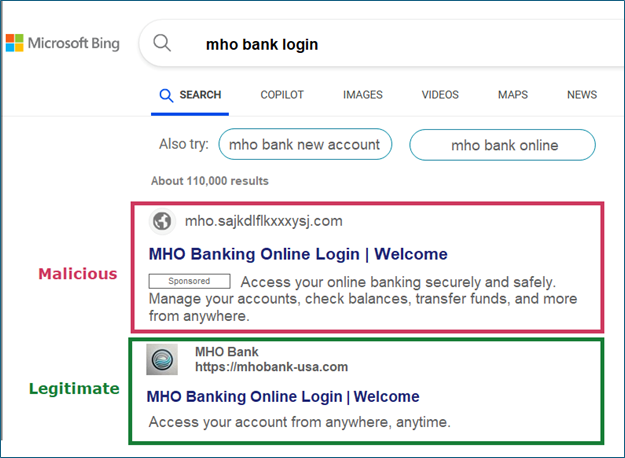
Sedara has observed some sophisticated practices in recent malvertising attacks:
- Attackers use multi-layered infrastructure that includes a benign landing page that they later change to redirect to a phishing site, likely to bypass the search engine’s safety checks for ads.
- The phishing site automatically passes credentials and MFA codes to the legitimate site, resulting in a valid session for the attacker.
- Attackers collect the user’s IP address and connect to the legitimate service through a botnet or VPN exit node that is geographically close to the victim. This makes the MFA prompt more believable.
- Using ephemeral sites that last only a few days at maximum, then moving on. This makes forensics and threat intelligence more difficult.
How can you protect against malvertising?
- Control client browsers. Disable or control browser plugins, and use client-based blockers or software to prevent ads from appearing or executing on your employees’ computers.
- Train users to use their own bookmarks or links to access information, and to check and recognize unusual URLs. Unusual behavior like error messages, delays, or redirected sites can also indicate a malicious site.
- Use a perimeter or client-based web filter to block categories like new domains (less than 30 days), or malicious websites.
- Report malicious links to the search engine to protect other users from being fooled.
Learn more about Phishing