Sedara Security Bulletin: NYSIC CAU Ransomware Variant

Summary (provided by NYSIC):
The New York State Intelligence Center (NYSIC) Cyber Analysis Unit (CAU) received updated current IOCs by a trusted 3rd party regarding a ransomware incident that is currently impacting networks belonging to a public entity in New York State. At this time, the ransomware variant remains unidentified. The incident started as a spear phishing campaign containing a malicious link and was activated before the environment’s network defense could neutralize it.
Mitigation Steps recommended by Sedara:
-
- Ensure endpoint security definitions and software are running and up-to-date.
- Consider limiting the use of PowerShell with Windows Group Policy or security products
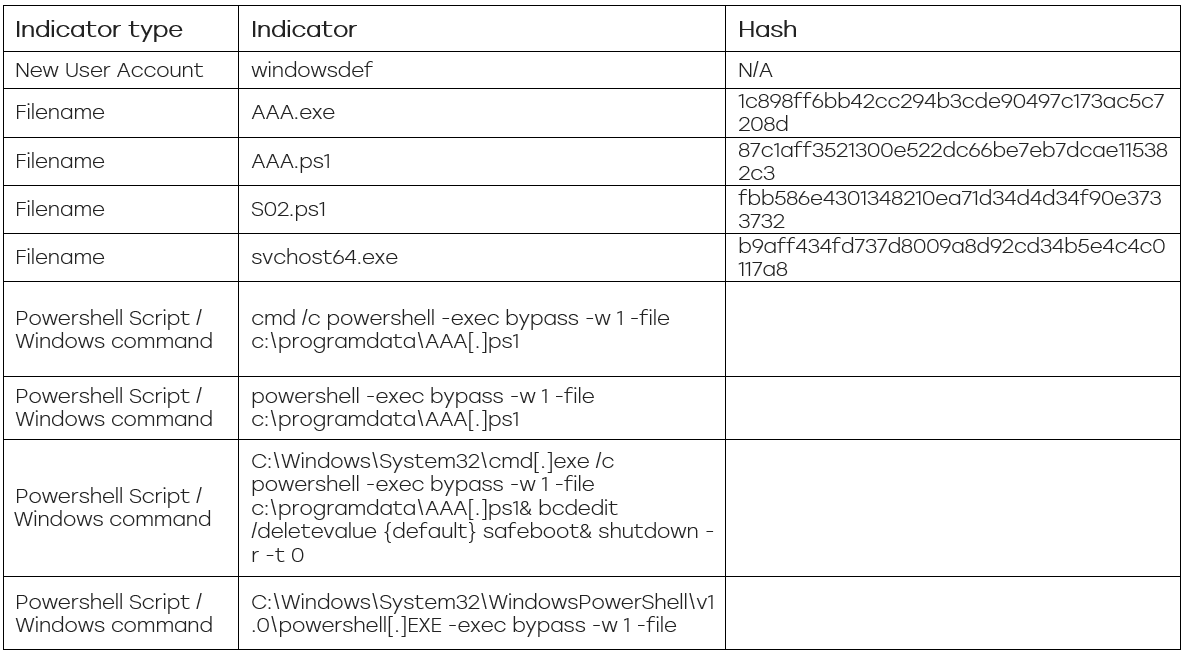
- Deny-list the security indicators shown below in security products.
Note: Remove defang brackets from indicators when entering these into security products.
What is Sedara doing to respond to this threat?
- Heightened attention to email and phishing alarms
- Blocking IOCs within EDR and antivirus services (if those services are provided by Sedara)
- Providing 24/7 coverage for assistance with security incidents
Want Help With a Security Incident?
Sedara can help your organization assess and address vulnerabilities and provide insight that prevents future incidents.
Get Future Compromise Alerts – Join Sedara Declassified
Subscribe to Sedara Declassified to get timely updates on new and evolving threats – and what to do about them – just like our clients do. And of course, if we can help you with anything directly, feel free to reach out.