Say Hello to the NIST CSF 2.0

Introduction
In August, NIST released the final draft of the highly anticipated update to its Cybersecurity Framework (CSF). The final draft is likely very close to what the final version will be when NIST releases it in early 2024. Therefore, it’s worth becoming familiar with the draft and beginning to plan how to use the NIST CSF 2.0 as a tool to strengthen your own cybersecurity posture. This article covers some of the most noteworthy features of the NIST CSF 2.0, including changes to the framework’s core and the new addition of implementation examples and an online reference tool.
Changes to the Core
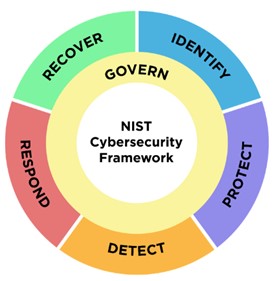
For most users, the NIST CSF’s most familiar feature is its core, the logically organized set of cybersecurity outcomes defined as functions, categories, and subcategories. NIST CSF 2.0 is updating information across all areas of the core. The most visible change is the introduction of Govern as the sixth function, stressing the importance of adopting leadership-sanctioned cybersecurity practices across the entire organization.
The six functions provide the highest-level outcomes of a cybersecurity program. In other words, successful cybersecurity programs are those that govern, identify, protect, detect, respond, and recover. The NIST CSF 2.0 includes new definitions for all of the functions:
| Govern (GV) | Establish and monitor the organization’s cybersecurity risk management strategy, expectations, and policy |
| Identify (ID) | Help determine the current cybersecurity risk to the organization |
| Protect (PR) | Use safeguards to prevent or reduce cybersecurity risk |
| Detect (DE) | Find and analyze possible cybersecurity attacks and compromises |
| Respond (RS) | Take action regarding a detected cybersecurity incident |
| Recover (RC) | Restore assets and operations that were impacted by a cybersecurity incident |
The next layer of the core is the categories that define more specific cybersecurity outcomes. There are 22 categories in the NIST CSF 2.0, which is one less than the previous version of the CSF. Many categories were shifted into the new Govern function, and an overall tightening of category language is found throughout the new framework.
|
Functions |
NIST CSF 2.0 Categories |
NIST CSF 1.1 Categories |
|
Govern (GV) |
Organizational Context (GV.OC) |
– |
|
Risk Management Strategy (GV.RM) |
– |
|
|
Cybersecurity Supply Chain Risk Management (GV.SC) |
– |
|
|
Roles, Responsibilities, and Authorities (GV.RR) |
– |
|
|
Policies, Processes, and Procedures (GV.PO) |
– |
|
|
Oversight (GV.OV) |
– |
|
|
Identify (ID) |
Asset Management (ID.AM) |
Asset Management (ID.AM) |
|
Risk Assessment (ID.RA) |
Business Environment (ID.BE) |
|
|
Improvement (ID.IM) |
Governance (ID.GV) |
|
|
– |
Risk Assessment (ID.RA) |
|
|
– |
Risk Management Strategy (ID.RM) |
|
|
– |
Supply Chain Risk Management (ID.SC) |
|
|
Protect (PR) |
Identity Management, Authentication, and Access Control |
Identity Management and Access Control (PR.AC) |
|
Awareness and Training (PR.AT) |
Awareness and Training (PR.AT) |
|
|
Data Security (PR.DS) |
Data Security (PR.DS) |
|
|
Platform Security (PR.PS) |
Information Protection Processes and Procedures (PR.IP) |
|
|
Technology Infrastructure Resilience (PR.IR) |
Maintenance (PR.MA) |
|
|
|
Protective Technology (PR.PT) |
|
|
Detect (DE) |
Continuous Monitoring (DE.CM) |
Anomalies and Events (DE.AE) |
|
Adverse Event Analysis (DE.AE) |
Security Continuous Monitoring (DE.CM) |
|
|
|
Detection Processes (DE.DP) |
|
|
Respond (RS) |
Incident Management (RS.MA) |
Response Planning (RS.RP) |
|
Incident Analysis (RS.AN) |
Communications (RS.CO) |
|
|
Incident Response Reporting and Communication (RS.CO) |
Analysis (RS.AN) |
|
|
Incident Mitigation (RS.MI) |
Mitigation (RS.MI) |
|
|
|
Improvements (RS.IM) |
|
|
Recover (RC) |
Incident Recovery Plan Execution (RC.RP) |
Recovery Planning (RC.RP) |
|
Incident Recovery Communication (RC.CO) |
Improvements (RC.IM) |
|
|
|
Communications (RC.CO) |
At the bottom of the core’s hierarchy are the subcategories, which define the most specific cybersecurity outcomes. Organizations using the NIST CSF typically spend the most time at the subcategory level. Here, organizations assess whether they are achieving the intent of the subcategory and, if not, develop action plans to implement new people, processes, or technology to improve their cybersecurity posture. There are 106 subcategories in the NIST CSF 2.0, two less than the previous version.
While it’s impractical to analyze all 106 subcategories here, the lessons drawn from analyzing a few can be applied to the rest. Examine, for instance, the new Platform Security (PR.PS) category and its six concomitant subcategories.
|
Platform Security (PR.PS): The hardware, software (e.g., firmware, operating systems, applications), and services of physical and virtual platforms are managed consistent with the organization’s risk strategy to protect their confidentiality, integrity, and availability |
PR.PS-01: |
|
PR.PS-02: |
|
|
PR.PS-03: |
|
|
PR.PS-04: |
|
|
PR.PS-05: |
|
|
PR.PS-06: |
This brand-new category covers a wide range of cybersecurity practices, including configuration management, hardware lifecycle management, software development and lifecycle management, and logging. Astute practitioners of the NIST CSF will notice that some cybersecurity practices, such as managing the onboarding, maintenance, and offboarding of software (i.e., software lifecycle management), manifest themselves across multiple subcategories, categories, and even functions (e.g., ID.AM-2 deals with maintaining software inventories). When using the NIST CSF as a tool to improve cybersecurity practices, it’s critical to be able to zoom in and out across the hierarchy of the functions, categories, and subcategories by following these general steps:
- Zoom in on each of the 106 subcategories and reflect on your organization’s practices against each of them. This is particularly helpful for uncovering an “aha moment” where you realize that an important practice isn’t being followed. Going subcategory-by-subcategory also enables a review of the full breadth of the CSF’s cybersecurity outcomes.
- Zoom out if you’re experiencing analysis paralysis and overwhelmed by the number of subcategories and the frequency with which one subcategory may appear slightly different than another. This is particularly helpful to realize the bigger-picture cybersecurity outcome, such as managing software across its entire lifecycle. You can also ignore the subcategories that don’t apply to you, such as PR.PS-06 if you don’t develop your own internal software.
Overall, NIST is changing language or adding new content across all of the functions, categories, and subcategories in the NIST CSF 2.0. New and returning users of the NIST CSF can start looking at the draft now and plan to complete a thorough review.
New Additions: Implementation Examples and Reference Tool
The NIST CSF 2.0 comes with two new additions that enhance the utility of the framework. The first are implementation examples, which serve as practical samples for what organizations might do to achieve the intent of each subcategory. These help clarify the purpose of each subcategory and generate new best practice ideas that organizations can adopt. For example, NIST cites the following implementation examples for the aforementioned PR.PS-02 subcategory:
|
PR.PS-02: |
Ex1: Perform routine and emergency patching within the timeframes specified in the Ex2: Update container images and deploy new container instances to replace rather than Ex3: Replace end-of-life software and service versions with supported, maintained versions Ex4:Uninstall and remove unauthorized software and services that pose undue risks Ex5:Uninstall and remove any unnecessary software components (e.g., operating Ex6: Define and implement plans for software and service end-of-life maintenance support and obsolescence |
Additionally, NIST has a new user-friendly web-based reference tool to explore the NIST CSF 2.0. The tool enables users to quickly sort through the CSF and export data in JSON or Excel format. The online tool will serve as the live repository for the implementation examples and informative references, which map each subcategory to other popular cybersecurity frameworks.
Conclusion
Overall, the NIST CSF is a powerful tool that organizations of all sizes can use to improve their own cybersecurity practices. Organizations can assess their current performance against the framework’s logical hierarchy of functions, categories, and subcategories and use the results to generate action plans for improvement. The NIST CSF 2.0 makes changes across all of the framework’s core and adds two additional resources in the form of implementation examples and an online reference tool. Although the NIST CSF 2.0 is still in draft and a final version isn’t expected until early 2024, organizations should make plans to include a review of the NIST CSF 2.0 as part of their cybersecurity, governance, and risk management practices.
Sedara can help organizations adopt the NIST CSF. Our Cybersecurity Development Program includes expert, dedicated virtual Chief Information Security Officers (vCISOs) who help organizations improve their cybersecurity posture and maintain regulatory compliance. Our vCISOs are fluent in the latest cybersecurity best practices and regulatory frameworks, including the NIST CSF. They can help meet the unique needs of your organization and guide teams on enhancing or implementing cybersecurity controls to reduce your risk.
More Reading on This Topic
- NIST CSF website: https://www.nist.gov/cyberframework
- More information on the released version of this topic: https://www.sedarasecurity.com/nist-csf-2-0-is-here-what-do-you-need-to-know/