What is Zero Trust
Introduction
Zero Trust is a cybersecurity philosophy that rejects the idea of offering implicit trust to traffic based on network location. In other words, Zero Trust views all traffic as potentially malicious, regardless of whether it originates from a traditionally trusted network source, and therefore requires all traffic to be scrutinized to determine whether access should be granted to a specific resource. The Zero Trust philosophy is gaining momentum, and more organizations are starting to engineer their architecture to include these principles. For example, in 2021 Executive Order 14208 mandated that the federal government move towards implementing Zero Trust Architecture. Likewise, the Department of Defense is currently reviewing its agencies’ proposals for Zero Trust implementation. However, non-federal and private-sector organizations can benefit from implementing these principles as well. This article explores what Zero Trust is and how organizations can adopt Zero Trust to reduce their cybersecurity risk.
Overview of Zero Trust
Zero Trust is an overarching philosophy and set of principles: it’s a security model, not a specific technological solution. Organizations that want to adopt Zero Trust principles can do so through a Zero Trust Architecture (ZTA) that implements the principles throughout their policies, processes, and data flows. This concept offers a different way of thinking about organizing and managing data flows that is more reflective of modern network security needs.
Traditional networks follow the “castle-and-moat” model where hardening techniques mainly focus on securing the network’s perimeter. Traditionally, “north-south” traffic, or external traffic that seeks to enter an internal network, is heavily scrutinized, such via a perimeter firewall. “East-west traffic”, or traffic that flows within an internal network, is typically not subject to the same rigorous security controls that are in place at the network’s perimeter. This philosophy moves beyond the focus on the network’s perimeter to instead focus on heavily scrutinizing all traffic, a process known as “deperimeterization.” There are two primary reasons for this philosophical shift: (1) modern networks don’t have as clear network perimeters as they used to due to the proliferation of cloud/hybrid environments and remote access solutions that make it more challenging to harden a single perimeter, and (2) malicious actors that penetrate a network perimeter can more easily move laterally within a network and escalate their privileges due to the implicit trust of their internal traffic. In traditional network environments, trusted users are implicitly granted access to large network segments whereas Zero Trust networks treat all users as untrusted and require explicit authorization to access specific resources. Therefore, adopting these principles can reduce risks faced in modern networks by scrutinizing all traffic across an organization’s complex environment.
Zero Trust Principles and Pillars
The Zero Trust security model is made up of several key security principles that organizations should reflect on how to incorporate them into their own environments:
- Treat all data, devices, applications, and services as resources: all assets are resources that deserve protection
- Never trust, always verify. All traffic, regardless is location, is treated as untrusted and must be granted explicit approval for access to resources
- Access decisions are based on dynamic, contextual factors, not just a valid credential or familiar IP address. Access decisions can be based on known users and devices; valid credentials; security profiles; time, date, and location; previous activity; and behavioral analysis
- Access is granted only for a single session, according to least privilege, in the most granular way possible, and with the smallest trust zone as possible. Users should be granted access to specific resources based on their access request, no more than what their legitimate business needs require. Access to one resource does not guarantee access to another resource. Access for one session does not guarantee access for subsequent sessions
- Access is continuously monitored and logged, and all network activity is monitored and logged, even after access is granted. Access that does not comply with security policy is revoked
Many organizations, including CISA, DoD, and NSA, have visualized Zero Trust principles existing among the pillars of modern networks. These principles can be applied to users, devices, applications and workloads, data, and the network environment, all of which are support by automation, monitoring, and analytics. The NSA (https://media.defense.gov/2023/Mar/14/2003178390/-1/-1/0/CSI_Zero_Trust_User_Pillar_v1.1.PDF) offers the following visual:
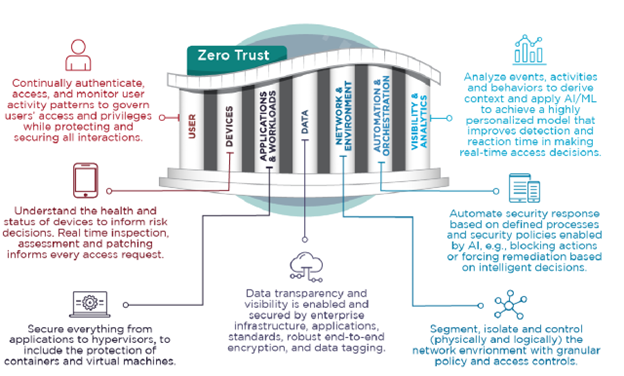
Zero Trust principles are an idealized goal, so actual implementations may be limited by technological, monetary, or procedural impediments. However, not being able to fully or uniformly implement a Zero Trust Architecture based on Zero Trust principles should not dissuade an organization from implementing some Zero Trust solutions. Security gains can be realized, even if Zero Trust Architecture is implemented for just a few data flows.
How Does Zero Trust Work?
Implementing a Zero Trust Architecture includes many different security controls and solutions, such as identity management systems (e.g., Activity Directory), Network Access Control (NAC) systems, Security Information and Event Management (SIEM) systems, data classification policies, Public Key Infrastructure (PKI), and threat intelligence feeds. All of these solutions can help achieve Zero Trust principles, such as requiring analysis and explicit approval for requests to access resources.
In addition to the aforementioned solutions, NIST SP 800-207 defines the primary means to implement Zero Trust Architecture: Policy Decision Points (PDPs) and Policy Enforcement Points (PEPs).
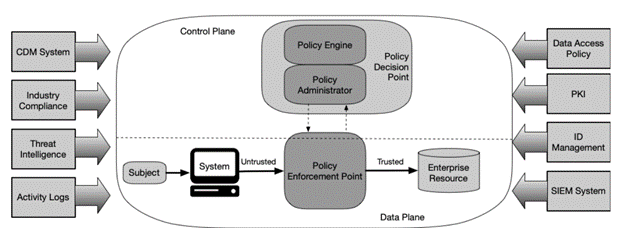
The PDP is where the decision to allow or deny access to a resource is made. The PDP analyzes various dynamic, contextual factors about the access request to determine if the requestor should be allowed access to the resource. Data from the aforementioned security solutions, such as NAC and SIEM systems, feed into the PDP to help inform the access decision. The PEP is where the actual connection between a requester and resource takes place. If the PDP allows access to a resource, the decision is passed to the PEP which established the authorized connection. The PEP commonly manifests as software agents on client devices, gateway hardware or software components in front of resources, or a portal that provides access.
Many major IT companies that offer networking technology offer agent-based or cloud-based solutions that serve as PDPs and PEPs.
From Zero to Hero: A Roadmap for Zero Trust Implementation
Implementing Zero Trust Architecture requires a variety of technology solutions that will likely need to be iteratively configured and deployed for different data flows over times. Organizations like CISA have defined a Zero Trust maturity model, linked below, that can guide implementations. However, organizations can follow the same general roadmap to begin implementing these principles.
- Identify your users – fully inventory your users, create organization-sanctioned identities that can be verified by a PDP, and define their access permissions according to least privilege
- Identify your assets – fully inventory your assets, define what resources will be protected, and implement logging and monitoring on assets
- Identify key risks, business processes, and data flows – define how data flows across your network, where access control can be enforced in the smallest trust zone possible, and where your organization’s greatest risks and most critical process flows are
- Identify which business process or data flow to protect first – define where to start implementing these solutions; while it’s tempting to begin with your most critical data flow, it may be easier to start with a smaller test case
- Identify Zero Trust implementation options – define which Architecture solutions will be used, such as an agent-based or cloud-based approach, microarchitecture, or software-defined networking, and how NAC, SIEM, identity management, data classification, PKI, and threat intelligence data will inform access decisions
- Test Zero Trust implementation solutions – analyze solution performance and logging and monitoring capabilities, and make adjustments as necessary before expanding Zero Trust Architecture solutions to other processes and workflows
Conclusion
Overall, Zero Trust is a security philosophy that treats all traffic as potentially malicious, requiring rigorous authentication decisions to be made for each access request to a resource. The model can help reduce cybersecurity risks by limiting the extent to which malicious actors can move laterally across a network. Federal agencies are in the process of implementing Zero Trust Architecture to harden their networks. However, non-federal and private sector organizations can also implement these solutions. All organizations should reflect on their network architecture to determine how access decisions are made and what access users are granted, whether implicitly or explicitly.
Sedara can help organizations strengthen their networks. Our Security Operations Center (SOC) is staffed 24x7x365 by expert analysts who monitor networks and alert on suspicious activity using SIEM technology. Also, our Cybersecurity Development Program includes expert, dedicated virtual Chief Information Security Officers (vCISOs) who help organizations improve their cybersecurity posture through enhancing or implementing new security solutions.
More Reading on This Topic
- NIST SP 800-207: Zero Trust Architecture: https://www.nist.gov/publications/zero-trust-architecture
- CISA Zero Trust Maturity Model: https://www.cisa.gov/zero-trust-maturity-model